Even before the Regulation (EU) No. 910/2014 on electronic identification (eID) and trusted services for electronic transactions in the internal market (eIDAS) became fully applicable on 1st of July 2016, a pan-European team of experts led by the Ruhr University Bochum and ecsec GmbH had joined forces in the EU-funded FutureTrust project to facilitate the provision and use of eID and trust services. In more than three years of intensive research and development, the FutureTrust project has produced numerous remarkable innovations, which are now being made available to the general public and outlined in the present blog post.
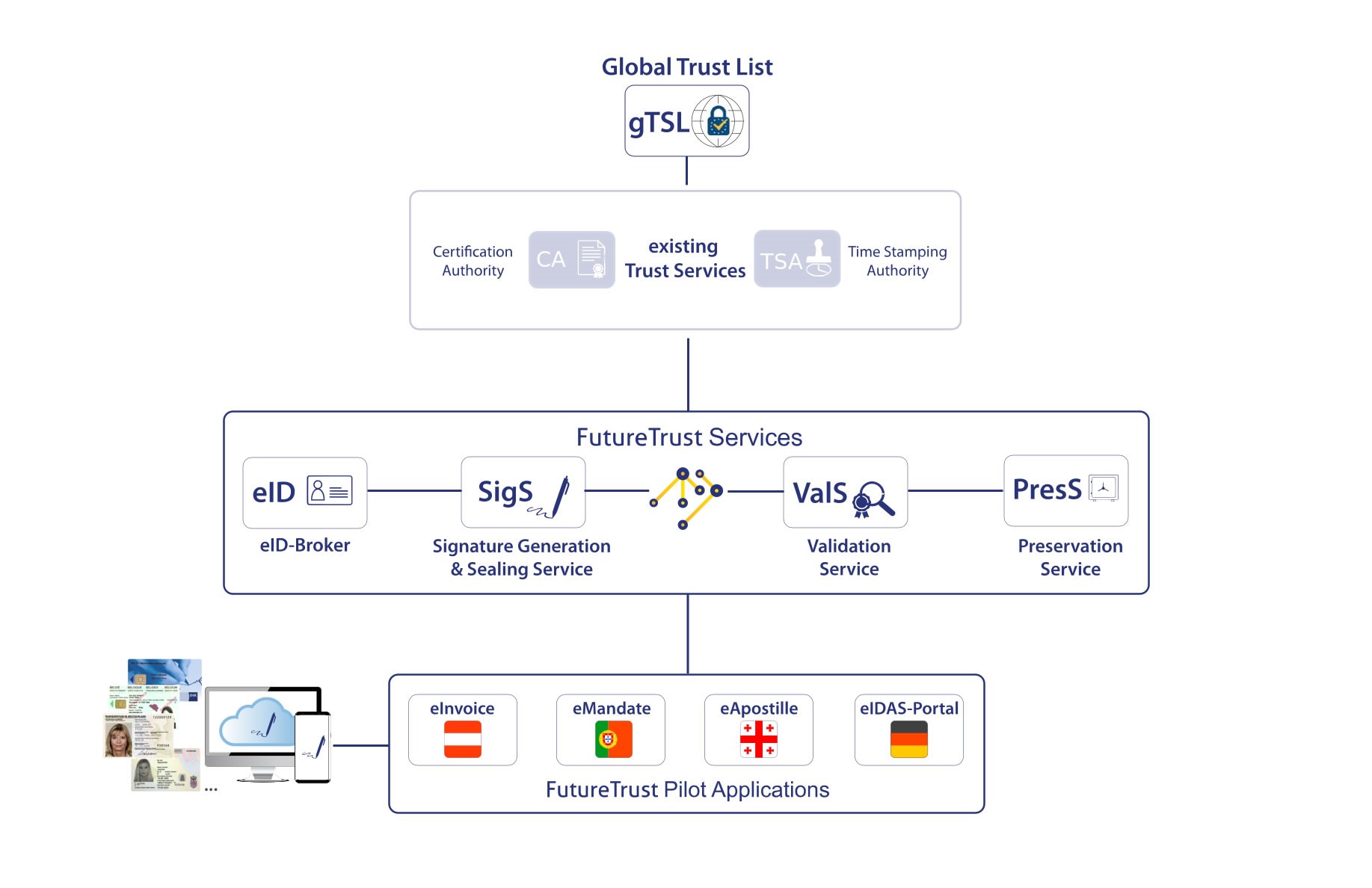
Overview of the FutureTrust System Architecture
As shown in the above figure, the FutureTrust project addresses large parts of the eIDAS-Ecosystem and integrates various FutureTrust Services and FutureTrust Pilot Applications as well as the “Global Trust List”, which provides information related to trust service providers across the European Member States and beyond.
There are the following basic FutureTrust Service
- Pan-European eID-Broker (eID-Broker, eID),
- Signature Generation & Sealing Service (SigS),
- Validation Service (ValS),
- Preservation Service (PresS),
and the following FutureTrust Pilot Applications
- a Portuguese service for electronic SEPA eMandates (eMandate),
- an Austrian service for electronic invoices (eInvoice),
- a Georgian service for electronic Apostilles (eApostille) and
- the German eIDAS-Portal, which allows to enrol for certificates after an eID-based identification.
Background, Motivation and Problems – as well as solutions provided by FutureTrust!
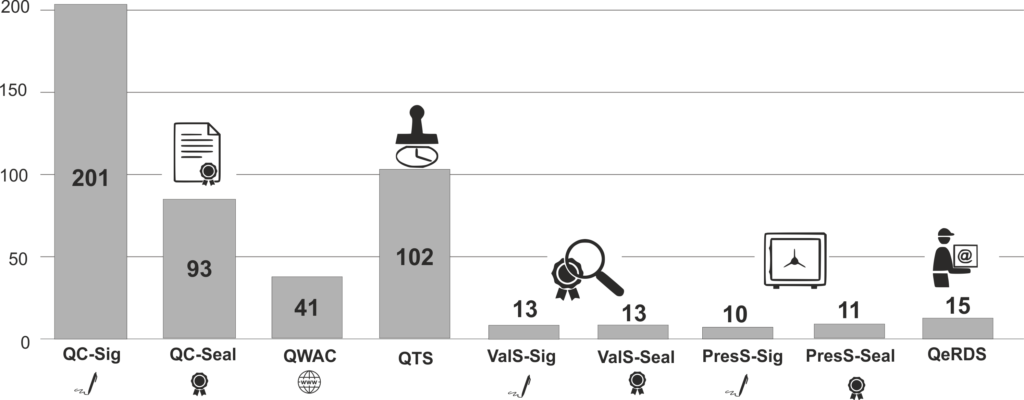
As shown in the figure below, there are currently[1] around 200 Qualified Trust Service Providers (QTSP) in Europe issuing qualified certificates for electronic signatures, as well as around 100 providers of qualified time stamps.
Hence, the eIDAS-Ecosystem is, with respect to these basic trust services, which already existed before the eIDAS-Regulation entered into force, fairly well developed. Similarly, there also exist a significant number of European providers of qualified certificates for issuing electronic seals (93) or website authentication (41). The development of the market seems to be on the right track here. On the other hand, there are very few providers of qualified validation (13), preservation (10 or 11) or electronic registered delivery service (15) so far. Furthermore the very promising option for issuing qualified certificates based on electronic identification (see Art. 24 (1) (b) of the eIDAS-Regulation) – especially in combination with remote signatures – does not yet seem to be practically implemented and available in the market.
Expecting this foreseeable development, the FutureTrust project has built upon experiences and previous work from pertinent projects (e.g. STORK, STORK 2.0, FutureID, e-SENS, SD-DSS, Open eCard, OpenPEPPOL and SkIDentity) in order to close the existing gaps as far as possible by adressing the following problems (P1-P6) and provide tailormade solutions (->):
- No Open Source Validation Service -> The FutureTrust Validation Service (ValS)
- No standardised Preservation Service -> The FutureTrust Preservation Service (PresS)
- No eID-based certificate enrolment -> The eIDAS-Portal of the German Universities
- No universal signature and seal creation service -> The FutureTrust Signature Generation & Sealing Service (SigS)
- Cross-border and non-European transactions are challenging -> The pan-European eID-Broker
- Demand for fundamental research in the area of security, trust and reliability
P1. No Open Source Validation Service -> The FutureTrust Validation Service (ValS)
Many currently available components for validating electronic signatures and seals are
- limited to specific document and signature formats (e.g. the freely available Adobe Reader only supports the validation of electronic signatures and seals in the PAdES format according to ETSI EN 319 142),
- have been shown to be vulnerable and / or
- are proprietary components, for which the sources are not publicly available
and hence the trustworthiness of a specific validation result is very difficult to assess.
Furthermore, as shown in the figure above, there are currently very few qualified validation service for qualified electronic signatures or seals available in Europe.
Against this background, the FutureTrust project has developed a comprehensive Validation Service (ValS), which supports advanced electronic signatures and seals (AdES) as well as related signature objects including X.509 certificates or Evidence Records based on configurable “Signature Validation Policies” and returns the validation result in a machine-readable XML or JSON based validation report (cf. ETSI TS 119 102-2 and OASIS DSS v1.0 Comprehensive Multi-Signature Verification Report Profile).
|
Format |
Standard |
Description |
|
CAdES |
ASN.1-based digital signature based on the “Cryptographic Message Syntax“ |
|
|
XAdES |
XML-based digital signature based on the “XML Digital signature“ |
|
|
PAdES |
PDF document with embedded CAdES signature |
|
|
JWS |
JSON-based digital signature for web applications, in the future also JAdES |
|
|
X.509 |
Allows to check the status and trustworthiness of an X.509 certificate (see also RFC 5280) based on a suitable Trusted List. |
|
|
ERS |
Evidence Records, which allow to produce efficient proofs of existence. |
More details with respect to the FutureTrust Validation Service (ValS), which will soon be provided as Open Source, will be provided in a forthcoming blog post.
P2. No standardised Preservation Service -> The FutureTrust Preservation Service (PresS)
The well-known fact that signed objects lose their evidential value, if cryptographic algorithms become weak, induces major challenges for applications, which require maintaining the integrity and authenticity of signed data for long periods of time – or even for eternity. While the Technical Guideline BSI TR-03125 (TR-ESOR) had specified components for the preservation of evidence before the advent of FutureTrust, the corresponding ETSI standards for preservation services, such as ETSI TS 119 511 and ETSI TS 119 512 only appeared recently.
Against this background, selected experts from the FutureTrust team have been actively involved in the preservation-related standardisation work within OASIS DSS-X and ETSI ESI such that FutureTrust project has been able to provide a reference implementation of selected preservation schemes from the new preservation standards.
More details with respect to the FutureTrust Preservation Service (PresS) will be provided in a forthcoming blog post.
P3. No eID-based certificate enrolment -> The eIDAS-Portal of the German Universities
Before a qualified trust service provider can issue a qualified certificate to a natural or legal person, it is obliged (see Art. 24 (1) of the eIDAS-Regulation) to verify the identity and, if applicable, any specific attributes of the certificate subject. Furthermore, there are similar requirements for non-qualified certificates, which are issued within the Public-Key Infrastructure of the German Research Network (Deutsches Forschungsnetz, DFN-PKI), which is audited against ETSI EN 319 411-1, and which can be used for electronic signatures, email encryption, authentication or website authentication. In addition to the classical way to perform the identity verification while the subject is physically present (Art. 24 (1) a)), the eIDAS-Regulation also allows to perform the identification remotely using appropriate electronic identification (eID) means (Art. 24 (1) b)), by using qualified signatures or seals (Art. 24 (1) c)) or other identification methods recognised at national level (Art. 24 (1) d)), if they provide equivalent assurance. While the growing number of notified eID schemes and the availability of the pan-European eID-Broker infrastructures strongly suggest to use eID means for the identity verification during certificate enrolment, this option does not seem to be available in practice yet. Against this background, the FutureTrust project has designed and implemented a smart eID-based system for certificate enrolment, which allows to combine University-specific credentials with eID-based identity verification in order to end up with a completely electronic process for certificate enrolment within the DFN-PKI.
More details with respect to this novel certificate enrolment system, which is referred to as the “eIDAS-Portal” of the German Universities, which are participating in FutureTrust, will be subject of a forthcoming blog post.
P4. No universal signature creation service -> The FutureTrust Signature Generation & Sealing Service (SigS)
Even if certificates are already issued, this does not mean that these certificates can easily be used to create signatures or seals in web applications. A universal service for using arbitrary smart card- or remote signature-based certificates of different providers does not seem to exist so far. Through the development of the ChipGateway-protocol by ecsec GmbH and LuxTrust S.A. and the extension and adaptation of the protocol and architecture to support the special features of the German eID card, as well as the latest standards developed by OASIS DSS-X and ETSI ESI, the FutureTrust project has provided a solid corner stone for the envisioned universal signature creation service.
More details with respect to the FutureTrust Signature Generation & Sealing Service (SigS) as well as the related standards produced by OASIS and ETSI will subject of a forthcoming blog post.
P5. Cross-border and non-European transactions are challenging -> The pan-European eID-Broker
Chapter II of the eIDAS-Regulation, which deals with eID systems, aims at creating a standardised interoperability framework with well-defined processes, security levels, minimum requirements and interfaces, but does not intend to harmonise the respective national eID systems. In doing so, the EU Member States can notify their national eID scheme, such that the corresponding eID means will be recognised across Europe for a certain level of assurance, after a careful assessment (“peer review”) has been conducted and the formal notification procedure has concluded with a publication in the Official Journal of the European Union (see 2019/C 150/06 for example). For the technical implementation of the eID interoperability framework, so-called „eIDAS-Nodes“ are provided, which take care about cross-border processes between the application services and the identification services. So far, the envisioned „eIDAS-Nodes“ are not completely available in production yet and the focus of the “eIDAS-Cooperation Network” is limited to EU Member States and countries in the European Economic Area.
Against this background, the FutureTrust project has built upon previous work from pertinent projects, such as FutureID and SkIDentity in order to develop a smart pan-European eID-Broker, which is protected by the European patents EP2439900 and EP2919145, supports a plenty of standards as well as notified eID means from Germany, Estonia, Luxembourg, Belgium and Portugal and is subject of a forthcoming blog post.
While cross-border identification within Europe is often not easy in practice, the electronic processing of transactions with non-European partners poses additional challenges related to data protection specifics in case of transferring personal data to third countries (cf. GDPR, chapter 5) and missing international agreements for mutual recognition of trust services according to Article 14 of the eIDAS-Regulation. Unfortunately, there is no global legislation comparable to the eIDAS-Regulation, which made it necessary in FutureTrust to conduct fundamental research in the area of legal, organisational and technical aspects, which are reflected in relevant academic publications and the prototype of a “Global Trust List” (gTSL). The gTSL is an Open Source component for the trusted management of trust lists according to ETSI TS 119 612, which can be deployed with the other FutureTrust services or as standalone service and which will be subject of a forthcoming blog post.
P6. Fundamental research demand in the area of security, trust and trustworthiness
Conducting security research regularly points out new security problems and vulnerabilities, and with respect to the central concepts of “Trust” and “Trustworthiness”, there does not even seem to be well-founded and generally accepted definitions – not to talk about globally accepted graded minimum requirements. Therefore, it was necessary to scientifically discuss and analyse these fundamental aspects of „Trust“ and „Trustworthiness“ within the FutureTrust project, before formal models were developed, which describe comprehensive “Trust Models”, which finally formed the basis for the objective comparison of trustworthiness of various identification and trust services.
Summary, Acknowledgement and Outlook
The present blog post provided a compact overview of the main problems addressed and solved within the FutureTrust project, which started on 1st of June 2016 and has received funding by the European Commission within the EU Framework Programme for Research and Innovation (Horizon 2020) under the Grant Agreement No. 700542.
As explained throughout this article, the FutureTrust project has conducted fundamental research with respect to the foundations of trust and trustworthiness, has actively supported the standardization process in relevant areas, and has developed numerous services, which ease the use of eID and electronic signature technology in real world applications by addressing the problems outlined above.
The practical applicability of the concepts and software components has been demonstrated in several pilot applications, such as a Portuguese service for electronic SEPA eMandates, an Austrian service for electronic invoices (eInvoice), a Georgian service for electronic Apostilles (eApostille) and last but not least the German eIDAS-Portal, which allows to enrol for certificates after an eID-based identification.
The FutureTrust Services and the FutureTrust Applications are now being made available to the general public step by step and interested parties are encouraged to get in touch with the FutureTrust experts to talk about tailormade solutions and individual needs.
[1] Comparing the current figures (July 2019) with the figures from a recent German article, which has appeared in DuD 2019/04, shows that the number of qualified trust service providers is slightly growing.



 [Michelau, January 12th 2016] SkIDentity uses the new version of the Open eCard App, which has recently be certified by the German Federal Office for Information Security (Bundesamt für Sicherheit in der Informationstechnik,
[Michelau, January 12th 2016] SkIDentity uses the new version of the Open eCard App, which has recently be certified by the German Federal Office for Information Security (Bundesamt für Sicherheit in der Informationstechnik,